NSA Criminals Hacked Over 100000 Computers – Radio Wave Back Door Makes Systems Hackable Even While Offline
The criminals in Obama’s corrupt NSA have really gone off the deep end when it comes to their out-of-control warrantless spying on innocent Americans.
In the past few months, we have learned about many unconstitutional crimes being committed by Obama’s NSA, and now we learn that the NSA has hacked over 100,000 computer systems, making the systems hackable by the NSA from miles away, and even if the computer is not connected to an Internet connection.
NSA Criminals can use radio waves to access back-doors they added to the computer systems to be able to gain access to the files stored on the NSA-hacked computers.
So the criminally-corrupt NSA is reading all of our emails, text messages, social media posts, collecting phone data from trillions of cell phones everyday, and now Obama’s corrupt NSA is taking over disconnected personal computers with back-door software that allows them to hack into the system using radio waves.
Maybe hackers worldwide will give the NSA a taste of their own medicine and start to hack the NSA, bringing down the most corrupt and dangerous organization in the world today.
Thank you Edward Snowden for opening our eyes to the criminal actions of Obama’s NSA. You are a hero to true American Patriots!
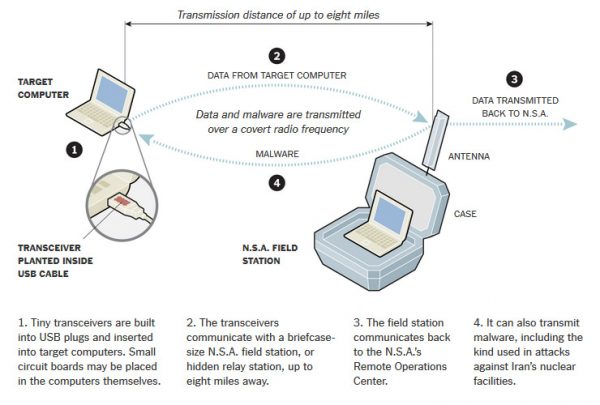
The National Security Agency has implanted software in nearly 100,000 computers around the world that allows the United States to conduct surveillance on those machines and can also create a digital highway for launching cyberattacks.
While most of the software is inserted by gaining access to computer networks, the N.S.A. has increasingly made use of a secret technology that enables it to enter and alter data in computers even if they are not connected to the Internet, according to N.S.A. documents, computer experts and American officials.
The technology, which the agency has used since at least 2008, relies on a covert channel of radio waves that can be transmitted from tiny circuit boards and USB cards inserted surreptitiously into the computers. In some cases, they are sent to a briefcase-size relay station that intelligence agencies can set up miles away from the target.
The radio frequency technology has helped solve one of the biggest problems facing American intelligence agencies for years: getting into computers that adversaries, and some American partners, have tried to make impervious to spying or cyberattack. In most cases, the radio frequency hardware must be physically inserted by a spy, a manufacturer or an unwitting user.
The N.S.A. calls its efforts more an act of “active defense” against foreign cyberattacks than a tool to go on the offensive. But when Chinese attackers place similar software on the computer systems of American companies or government agencies, American officials have protested, often at the presidential level.
Among the most frequent targets of the N.S.A. and its Pentagon partner, United States Cyber Command, have been units of the Chinese Army, which the United States has accused of launching regular digital probes and attacks on American industrial and military targets, usually to steal secrets or intellectual property. But the program, code-named Quantum, has also been successful in inserting software into Russian military networks and systems used by the Mexican police and drug cartels, trade institutions inside the European Union, and sometime partners against terrorism like Saudi Arabia, India and Pakistan, according to officials and an N.S.A. map that indicates sites of what the agency calls “computer network exploitation.”
“What’s new here is the scale and the sophistication of the intelligence agency’s ability to get into computers and networks to which no one has ever had access before,” said James Andrew Lewis, the cybersecurity expert at the Center for Strategic and International Studies in Washington. “Some of these capabilities have been around for a while, but the combination of learning how to penetrate systems to insert software and learning how to do that using radio frequencies has given the U.S. a window it’s never had before.”
Stand Up To Government Corruption and Hypocrisy – usbacklash.org
